"Our goal is not to get at the systems but to find all the ways to get there."
1. Enumeration Methodology
[Infrastructure-based enumeration]
1) Internet Presence:
- Identification of Internet presence and externally accessible infrastructure.
- Domains, Subdomains, vHosts, ASN, Netblocks, IP Addresses, Cloud Instances, Security Measures
- The goal of this layer is to identify all possible target systems and interfaces that can be tested.
2) Gateway:
- Identify the possible security measures to protect the company's external and internal infrastructure.
- Firewalls, DMZ, IPS/IDS, EDR, Proxies, NAC, Network Segmetation, VPN, Cloudflare.
- The goal is to undersrand what we are dealing with and what we have to watch out for.
[Host-based enumeration]
3) Accessible Services:
- Identify accessible interfaces and services that are hosted externally or internally.
- Service Type, Functionality, Configuration, Port, Version, Interface
- This layer aims to understand the reason and functionality of the target system and gain the necessary knowledge to communicate with it and exploit it for our purposes effectively.
4) Processes:
- Identify the internal processes, sources, and destinations associated with the services.
- PID, Processed Data, Tasks, Source, Destination
- Processes have to perform specific tasks, and such tasks have at least one source and one target. The goal here is to understand these factors and identify the dependencies between them.
[OS-based enumeration]
5) Privileges:
- Identification of the internal permissions and privileges to the accessible services.
- Groups, Users, Permissions, Restrictions, Environment
6) OS Setup:
- Identification of the internal components and system setup.
- OS Type, Patch Level, Network config, OS Environment, Configuration files, sensitive private files
2. Domain Information
1) Online Presence
(1) SSL certificate
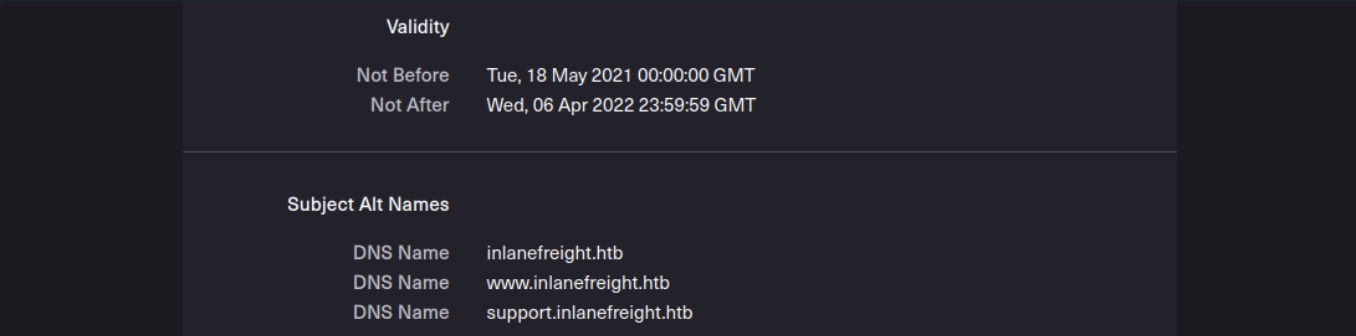
(2) Certificate Transparency logs: crt.sh: https://crt.sh/
crt.sh | Certificate Search
crt.sh
we can get a list of subdomains.
yeon0815@htb[/htb]$ curl -s https://crt.sh/\?q\=inlanefreight.com\&output\=json | jq . | grep name | cut -d":" -f2 | grep -v "CN=" | cut -d'"' -f2 | awk '{gsub(/\\n/,"\n");}1;' | sort -u
account.ttn.inlanefreight.com
blog.inlanefreight.com
bots.inlanefreight.com
console.ttn.inlanefreight.com
ct.inlanefreight.com
data.ttn.inlanefreight.com
*.inlanefreight.com
inlanefreight.com
integrations.ttn.inlanefreight.com
iot.inlanefreight.com
mails.inlanefreight.com
marina.inlanefreight.com
marina-live.inlanefreight.com
matomo.inlanefreight.com
next.inlanefreight.com
noc.ttn.inlanefreight.com
preview.inlanefreight.com
shop.inlanefreight.com
smartfactory.inlanefreight.com
ttn.inlanefreight.com
vx.inlanefreight.com
www.inlanefreight.com(3) company hostes servers
we can identify the hosts directly accessible from the Internet and not hosted by third-party providers. This is because we are not allowed to test the hosts without the permission of third-party providers.
yeon0815@htb[/htb]$ for i in $(cat subdomainlist);do host $i | grep "has address" | grep inlanefreight.com | cut -d" " -f1,4;done
blog.inlanefreight.com 10.129.24.93
inlanefreight.com 10.129.27.33
matomo.inlanefreight.com 10.129.127.22
www.inlanefreight.com 10.129.127.33
s3-website-us-west-2.amazonaws.com 10.129.95.250(4) Shodan - IP list
shodan can be used to find devices and systems permanently connected to the Internet like IoT. It searches the Internet for open TCP/IP ports and filters the systems according to specific terms and criteria.
yeon0815@htb[/htb]$ for i in $(cat subdomainlist);do host $i | grep "has address" | grep inlanefreight.com | cut -d" " -f4 >> ip-addresses.txt;done
yeon0815@htb[/htb]$ for i in $(cat ip-addresses.txt);do shodan host $i;done
10.129.24.93
City: Berlin
Country: Germany
Organization: InlaneFreight
Updated: 2021-09-01T09:02:11.370085
Number of open ports: 2
Ports:
80/tcp nginx
443/tcp nginx
10.129.27.33
City: Berlin
Country: Germany
Organization: InlaneFreight
Updated: 2021-08-30T22:25:31.572717
Number of open ports: 3
Ports:
22/tcp OpenSSH (7.6p1 Ubuntu-4ubuntu0.3)
80/tcp nginx
443/tcp nginx
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, -TLSv1.3, TLSv1.2
|-- Diffie-Hellman Parameters:
Bits: 2048
Generator: 2
10.129.27.22
City: Berlin
Country: Germany
Organization: InlaneFreight
Updated: 2021-09-01T15:39:55.446281
Number of open ports: 8
Ports:
25/tcp
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, TLSv1.2, TLSv1.3
53/tcp
53/udp
80/tcp Apache httpd
81/tcp Apache httpd
110/tcp
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, TLSv1.2
111/tcp
443/tcp Apache httpd
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, TLSv1.2, TLSv1.3
|-- Diffie-Hellman Parameters:
Bits: 2048
Generator: 2
Fingerprint: RFC3526/Oakley Group 14
444/tcp
10.129.27.33
City: Berlin
Country: Germany
Organization: InlaneFreight
Updated: 2021-08-30T22:25:31.572717
Number of open ports: 3
Ports:
22/tcp OpenSSH (7.6p1 Ubuntu-4ubuntu0.3)
80/tcp nginx
443/tcp nginx
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, -TLSv1.3, TLSv1.2
|-- Diffie-Hellman Parameters:
Bits: 2048
Generator: 2(5) DNS Records
DNS record are like phonebook entries for the internet. They map human-readable domain names (like inlanefreight.com) to specific information like IP addresses, mail servers, verification codes, etc.
yeon0815@htb[/htb]$ dig any inlanefreight.com
; <<>> DiG 9.16.1-Ubuntu <<>> any inlanefreight.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52058
;; flags: qr rd ra; QUERY: 1, ANSWER: 17, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;inlanefreight.com. IN ANY
;; ANSWER SECTION:
inlanefreight.com. 300 IN A 10.129.27.33
inlanefreight.com. 300 IN A 10.129.95.250
inlanefreight.com. 3600 IN MX 1 aspmx.l.google.com.
inlanefreight.com. 3600 IN MX 10 aspmx2.googlemail.com.
inlanefreight.com. 3600 IN MX 10 aspmx3.googlemail.com.
inlanefreight.com. 3600 IN MX 5 alt1.aspmx.l.google.com.
inlanefreight.com. 3600 IN MX 5 alt2.aspmx.l.google.com.
inlanefreight.com. 21600 IN NS ns.inwx.net.
inlanefreight.com. 21600 IN NS ns2.inwx.net.
inlanefreight.com. 21600 IN NS ns3.inwx.eu.
inlanefreight.com. 3600 IN TXT "MS=ms92346782372"
inlanefreight.com. 21600 IN TXT "atlassian-domain-verification=IJdXMt1rKCy68JFszSdCKVpwPN"
inlanefreight.com. 3600 IN TXT "google-site-verification=O7zV5-xFh_jn7JQ31"
inlanefreight.com. 300 IN TXT "google-site-verification=bow47-er9LdgoUeah"
inlanefreight.com. 3600 IN TXT "google-site-verification=gZsCG-BINLopf4hr2"
inlanefreight.com. 3600 IN TXT "logmein-verification-code=87123gff5a479e-61d4325gddkbvc1-b2bnfghfsed1-3c789427sdjirew63fc"
inlanefreight.com. 300 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com include:_spf.atlassian.net ip4:10.129.24.8 ip4:10.129.27.2 ip4:10.72.82.106 ~all"
inlanefreight.com. 21600 IN SOA ns.inwx.net. hostmaster.inwx.net. 2021072600 10800 3600 604800 3600
;; Query time: 332 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: Mi Sep 01 18:27:22 CEST 2021
;; MSG SIZE rcvd: 940[Record Types]
a. A: Address Records. Maps the domain to IP addresses.
b. MX: Mail Exchange Records. Specifies the mail servers to handle emails for the domain.
- 1 aspmx.l.google.com (highest priority mail server)
- 5 alt2.aspmx.l.google.com (backup mail server)
c. NS: Name Servers Records. Shows the authoritative name servers that hold the domain's DNS records.
d. TXT: Used for various purposese like domain verification and security policies.
e. SOA: Start of Authority Records. Contains info about the primary name server, email of the admin, and DNS settings.
3. Cloud Resources
AWS (Amazon) - S3 buckets
GCP (Google) - cloud storage
Azure (Microsoft) - blobs
[Different ways to find cloud storage]
1) Google search for AWS
- intext:{company_name} inurl:amazonaws.com
2) Google search for Azure
- intext:{company_name} inurl:blob.core.windows.net
3) Target Website - Source Code
4) domain.glass: https://domain.glass/
Domain DNS Record and WHOIS Information
domain.glass
5) GrayHatWarfare: https://buckets.grayhatwarfare.com/
Public Buckets by GrayhatWarfare
Regex Autocorrect Our system is build in such a way, so that the input regex must match the complete filename, start to end in order to be returned. Most people expect that if their regex matches partially in a filename this will be returned. Because not a
buckets.grayhatwarfare.com
6) Private and public SSH keys leaked
4. Staff
Searching for and identifying employees on social media platforms can also reveal a lot about the teams' infrastructure and makeup.
1) LinkedIn - Job post
2) LinkedIn - Employee #1 About
3) LinkedIn - Employee #2 Career
5. FTP
[In an FTP connection, 2 channels are opened]
1) TCP port 21: the client and server establish a control channel through port 21.
2) TCP port 20: both communication participants can establish the data channel via port 20. This channel is used exclusively for data transmission
[active vs passive]
1) active FTP: the client informs the server via which client-side port the server can transmit its responses. However, if a firewall protects the client, the server cannot reply because all external connections are blocked.
2) passive FTP: the server announces a port through which the client can establish the data channel. The firewall does not block the transfer.
[TFTP]
- Trivial File Transfer Protocol
- it does not provide user authentication
- while FTP uses TCP, TFTP uses UDP
- it sets limits on access based soley on the read and write permissions of a file in the OS.
[vsFTPd]
- One of the most used FTP servers on Linux-based distributions
- /etc/vsftpd.conf: default configuration
- /etc/ftpusers: this file is used to deny certain users access to the FTP service.
