1. Initial Enumeration with Nmap
We begin by scanning the target machine using nmap to identify open ports and running services
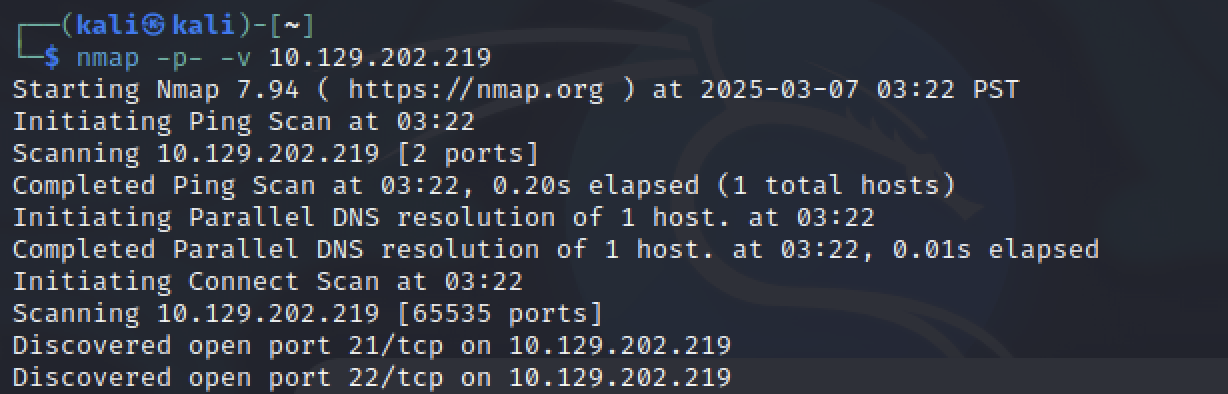

We have found there are 2 open ports, FTP(21), ssh(22)
2. FTP Bruteforce Attack
Since FTP is open, we attempt to brute-force the login credentials using wordlists, username.list and password.list.

We have found the login name and the password.
3. Accessing FTP and Extracting Sensitive Files
Using the obtained credentials, we log in to the FTP server and enumerate files.

During enumeration, we find an SSH private key file (id_rsa).
We download it to our local machine.
4. Logging into SSH with the Private Key
SSH private keys require proper permissions to be used for authentication.
Now, we use the downloaded private key to log into the machine via SSH.

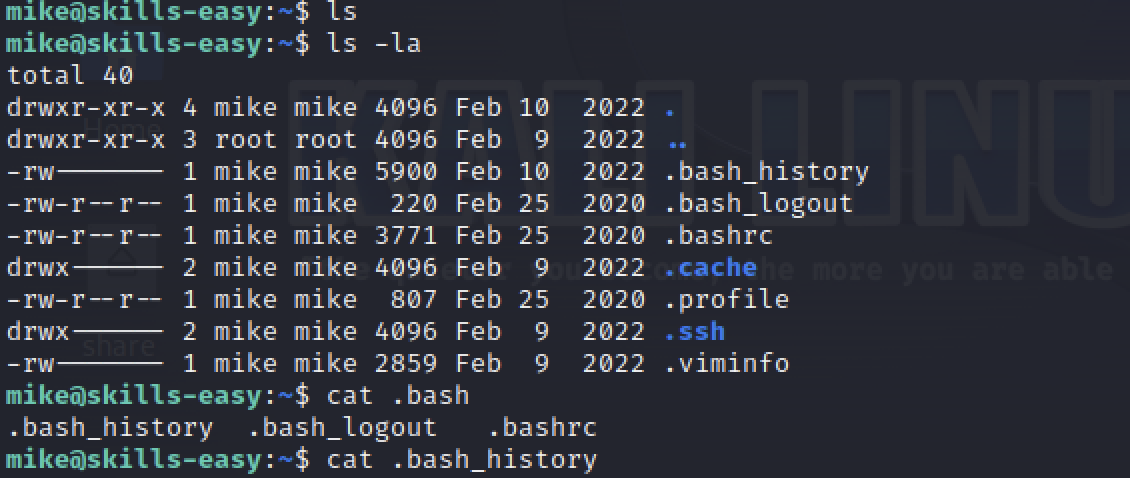
and we can find the root password in the bash history.
1. Initial Enumeration with Nmap
We begin by scanning the target machine using nmap to identify open ports and running services


We have found there are 2 open ports, FTP(21), ssh(22)
2. FTP Bruteforce Attack
Since FTP is open, we attempt to brute-force the login credentials using wordlists, username.list and password.list.

We have found the login name and the password.
3. Accessing FTP and Extracting Sensitive Files
Using the obtained credentials, we log in to the FTP server and enumerate files.

During enumeration, we find an SSH private key file (id_rsa).
We download it to our local machine.
4. Logging into SSH with the Private Key
SSH private keys require proper permissions to be used for authentication.
Now, we use the downloaded private key to log into the machine via SSH.

and we can find the root password in the bash history.

